Offsite Corporate Security
The issue of corporate security is becoming a larger threat as employees travel with their business machines and BYOD (bring your own) devices. The recent loss of a laptop with thousands of customer files including SSNs brings this issue to the forefront.
Although many steps can be applied to secure corporate data in the field, it would depend on who ends up with your CEO’s lost or stolen laptop and their skill level. For the most part, almost all devices have at least SOME type of password to enter the machines. If not, you have some serious security concerns at your business. The real problem is when you have the device in hand, even intermediate users can find the tools to defeat a simple Windows password. Microsoft has tried to limit the availability of their password reset tools, but have not been entirely successful. Just take a look at Craigslist in any city and browse how many ads there are offering to reset your Windows password for next to nothing.
Fortunately, we can address some of these issues with tools that the manufacturers have provided us. The BIOS or hard drive password is probably the most effective single tool that could provide at least some protection for your forgetful CEO that continues to leave his laptop at the local coffee shop. This can become an issue if you forget or lose the BIOS or hard drive password, as it’s next to impossible to defeat. If done correctly, this will secure the data on the hard drive, but could result an unusable device.
Next in line is securing the many BYOD devices employees bring to the table. You could of course completely ban all devices except IT department issued, but many corporate environments allow the use of at least email on BYOD as cost savings can be considerable. As most enterprises use Exchange, either in-house or in the cloud, there is a function to remotely wipe smartphones from within Exchange.
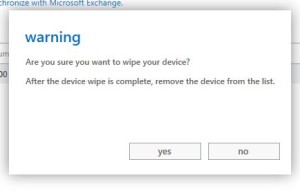
Hopefully you would never want to erase one of your employee’s phones, but you must secure your corporate data from prying eyes.
In summation, just these 2 steps in a corporate edict could end up saving your company a considerable amount of money, public reputation issues, and or legal ramifications.